Fraud Network Detection
Stay one step ahead of fraud with the new AI-based solution from Sumsub.
The Fraud Network Detection tool is a complex fincrime typology agnostic solution for clustering applicants based on similarities in their behavior and patterns of using technical capabilities. It significantly enhances control and helps you investigate different techniques across fincrime types.
The whole process is built and designed, including machine learning technology, to ensure constant improvements and faster fraudulent activity detection at both KYC and TM stages of verification.
When launching the tool, you will be able to access the following benefits:
- Prevent multi-accounting. Through network analysis, we unveil connections between accounts using similar templates or originating from the same IP addresses or devices.
- Boost deepfakes recognition. Uncover deepfakes looking for additional clues and use information on the found fraud networks to detect whole clusters of deepfakes.
- Combat chargebacks with enhanced mule detection. Development in detecting fraudulent networks allows us to actively participate in the ongoing arms race against deepfakes and combat against the mules, which are a popular form of fraud where another person's identity is purchased instead of being generated or stolen.
- Monitor traffic. By assessing completion speeds, geographical patterns, and other relevant parameters, we distinguish genuine user engagement from artificially motivated traffic, enhancing the overall reliability of your platform's user base.
- Detect bot farms. Via analysis of the device fingerprints, completion speeds, and other behavioral nuances, with Sumsub's Fraud Network Detection, we efficiently detect and neutralize the threat posed by bot farms, safeguarding your platform's integrity.
How Fraud Network Detection works
Sumsub's Fraud Network Detection shows connections between the applicants/clusters of applicants based on various parameters. Links between the applicants help you indicate suspicious activity and proactively investigate and intervene in criminal networks without relying on money movement as the sole trigger. According to the gathered information, your applicants can be clustered as follows:
- By device, IP address, cookies, Liveness device (Camera), and the address specified in PoA documents.
- By similar documents and selfies.
- By action time (e.g. many applicants related to the same device have been created in a short amount of time).
We calculate networks every day for the last 30 days with added documents or selfies through WebSDK or MobileSDK.
Get started with Fraud Network Detection
Almost nothing is needed to start detecting potential fraudulent patterns amongst your applicants:
- Contact your Customer Success Manager to implement Fraud Networks Detection in your verification process.
- Review the results on the criminal connections detected when verifying applicants.
Use WebSDK
The more data is shared with Sumsub and the more our services are used, the more illegal clusters can be detected, so WebSDK integration is preferable for such cases.
Review Fraud Network Detection results
You can find the results on the Fraud Network Detection findings in the following ways:
- Use the Sumsub API:
- To get the list of all fraud networks, use this method.
- To get the list of all fraud networks by
applicantId, use this method. - To get the fraud network by
networkId, use this method.
- In the Dashboard, go to the Applicants menu and select the Applicant Networks tab. Here, you can see the list of fraud networks associated with your applicants.
- In an applicant profile, scroll down to the Applicant Networks block and find information on the fraud networks related to the applicant.
The following table describes network properties available in the Dashboard:
| Property name | Description |
|---|---|
Network ID |
Shows a unique identifier of a network. |
Created |
Contains information on the date when a network was created. |
| Modified | Shows the date when the last applicant was added to the network. |
| Pattern |
Indicates the reasons for network creation and its similarities:
|
| Stats |
Shows the statistics based on the following parameters:
|
| Notes | Contains the notes that you have added to the case including the attached tags. |
Results can be downloaded as a CSV report as well and will contain information on all applicants included in the network. The following data will be available in the report:
| Value in report | Description |
|---|---|
id | A unique network identification number. |
createdAt | The time and date of the network creation. |
review.reviewStatus | A current verification status. |
review.reviewResult.reviewAnswer | A final verification result displaying the GREEN or RED status:
|
externalUserId | A unique applicant identifier in your system. |
addedAt | The time and date when the applicant was added to the network. |
View network data as table, chart, or map
When checking the network data, you can switch between the table and chart views:
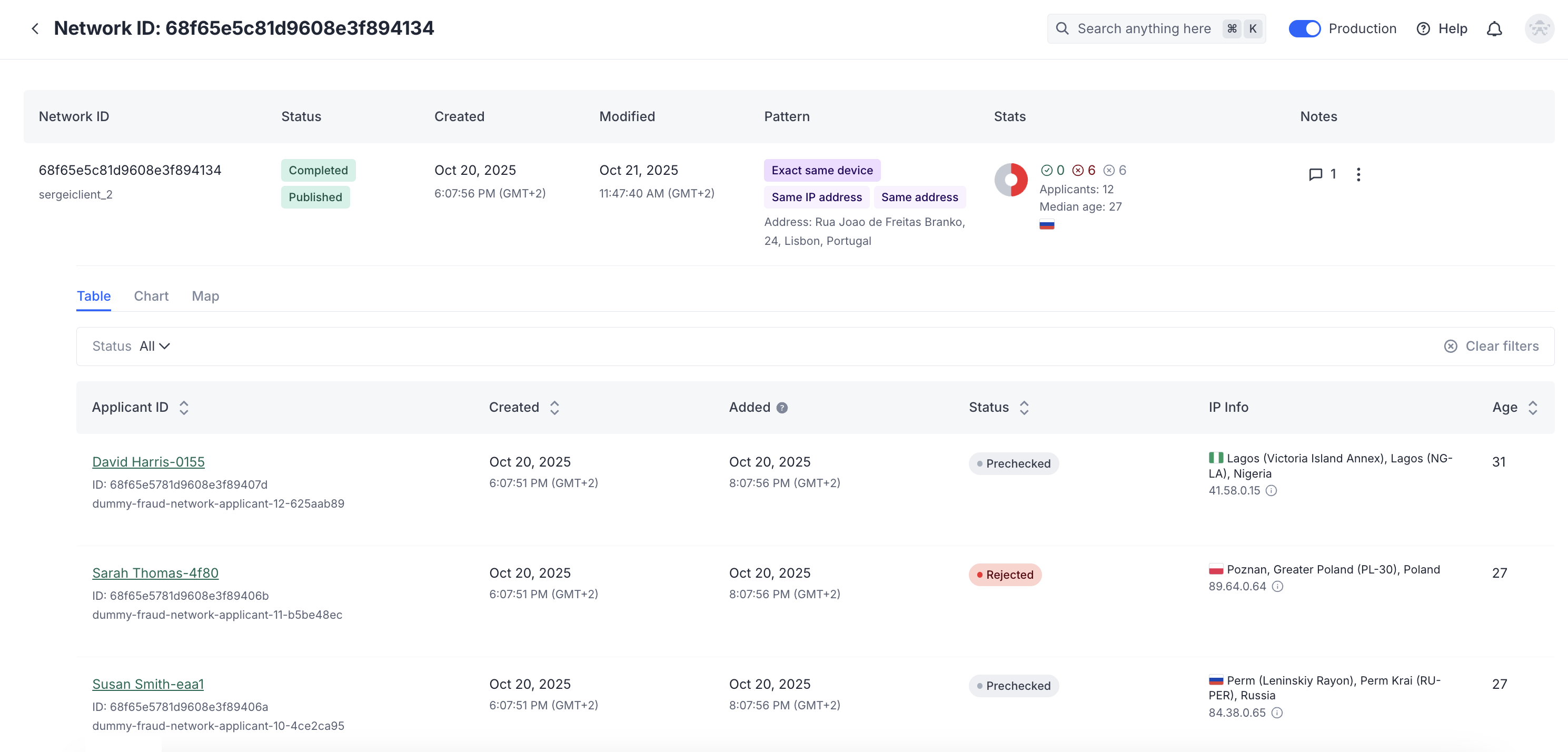
The table view shows the list of applicants with the links and all related information.
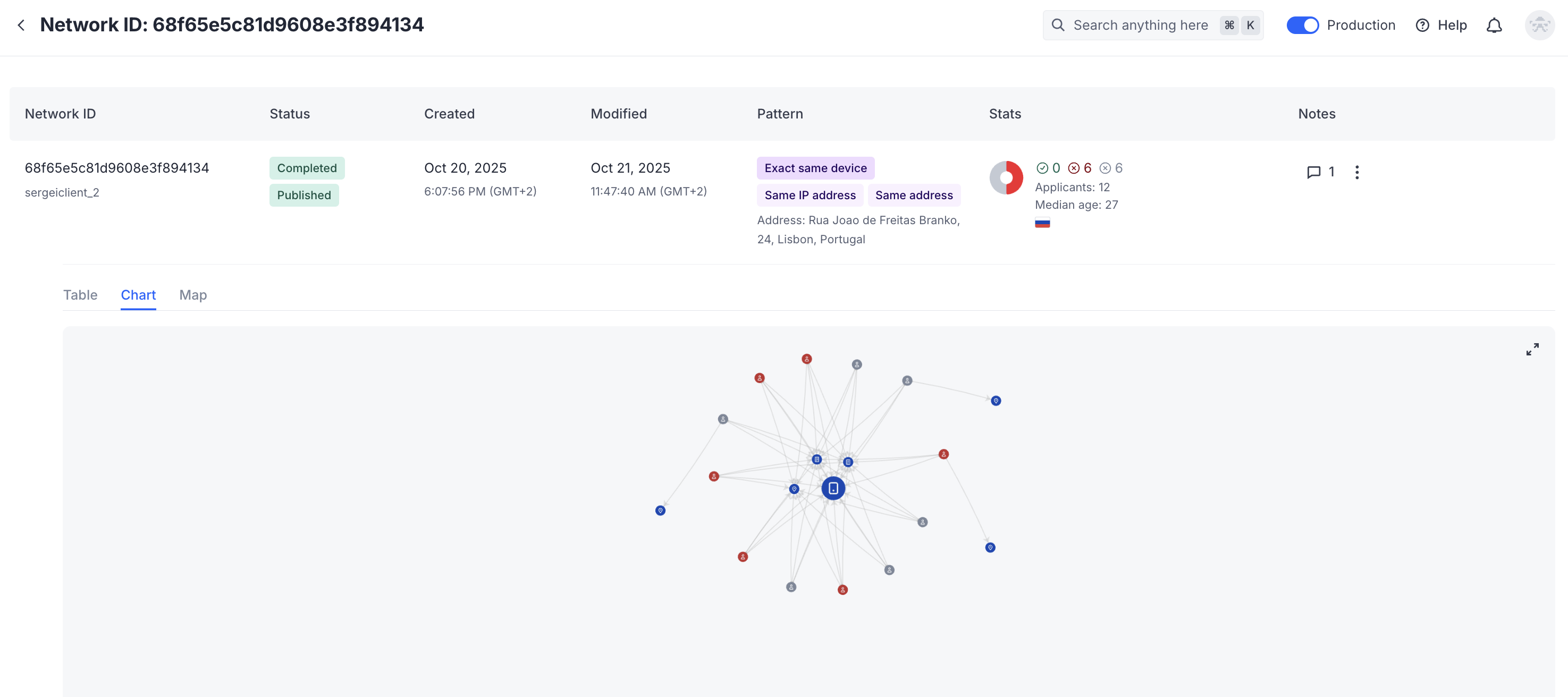
The chart displays applicants, their IP addresses, device fingerprints, and various templates as nodes connected by edges.
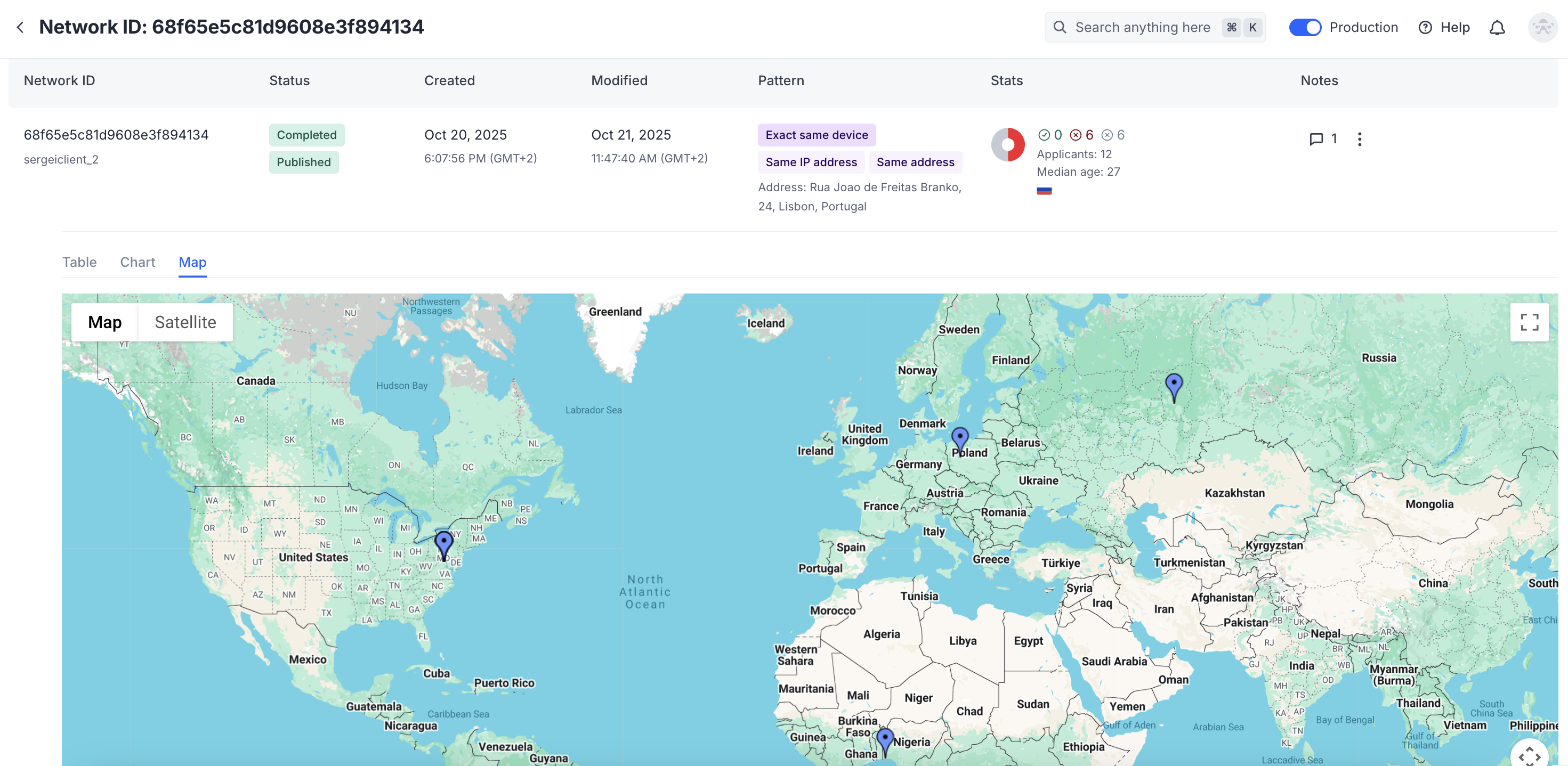
The map view shows the applicants’ locations on a global map based on their detected IP addresses.
Updated 3 months ago