Fraud Network Detection
Stay one step ahead of fraud with the new AI-based solution from Sumsub.
Fraud Network Detection helps you uncover hidden connections between applicants using all data available within the Sumsub platform. Instead of reviewing accounts one by one, you can see how they relate to each other — through shared devices, IPs, cookies, document templates, selfie images and selfie backgrounds, liveness signals, behavioral patterns, and other technical attributes.
The solution focuses on detecting coordinated or linked activity that would be impossible to identify at the single-applicant level. By analyzing both technical infrastructure and identity-level similarities, it surfaces patterns that indicate risks of organized or abusive behavior.
Fraud Network Detection is especially effective for:
- Detecting multi-accounting. Identify users who create multiple accounts to bypass rules and abuse the platform.
- Exposing account farms. Uncover large-scale account creation driven by shared infrastructure, automation, or repeated document and selfie patterns.
- Identifying money mules. Reveal networks of accounts created to be operated by third parties or used to move funds on behalf of others.
- Uncovering organized fraud rings. Pinpoint groups of individuals coordinating fraudulent activity, even when they use different identities, devices, or environments.
By shifting the focus from isolated applicant checks to relationship analysis across identity, behavioral, and technical signals, Fraud Network Detection enables proactive investigation of complex fraud schemes at scale.
How Fraud Network Detection works
Fraud Network Detection analyzes data collected during user verification across connected Sumsub services, including ID verification, address verification, Liveness checks, and Device Intelligence. It continuously evaluates this information to identify meaningful patterns that indicate connections between applicants.
As soon as the system detects a strong and reliable pattern — for example, shared device infrastructure, repeated document templates, similar selfie backgrounds, or behavioral overlaps — it links the relevant applicants into a network. More complex patterns may require additional data and time to accumulate before a confident connection can be established.
Once a pattern is confirmed, a new applicant network is created automatically. These networks are dynamic: if new applicants exhibit the same signals or behavioral characteristics, they are added to the existing network in real time.
You can review detected networks directly in the Dashboard or access it via API, allowing you to integrate network insights into your decision-making flows, automation logic, or investigation processes.
Get started with Fraud Network Detection
Almost nothing is needed to start detecting potential fraudulent patterns amongst your applicants:
- Contact your Customer Success Manager to implement Fraud Networks Detection in your verification process.
- Review the results on the criminal connections detected when verifying applicants.
Use WebSDK, MobileSDK and Device IntelligenceFraud Network Detection becomes more powerful as more data is available. The broader the signal coverage, the more accurately the system can identify hidden relationships and coordinated activity.
To maximize effectiveness, it is strongly recommended to enable Device Intelligence and use WebSDK or MobileSDK so that Sumsub can collect richer behavioral and technical signals during verification.
Review Fraud Network Detection results
You can find the results on the Fraud Network Detection findings in the following ways:
- Use the Sumsub API:
- To get the list of all fraud networks, use this method.
- To get the list of all fraud networks by
applicantId, use this method. - To get the fraud network by
networkId, use this method.
- In the Dashboard, go to the Applicants menu and select the Applicant Networks tab. Here, you can see the list of fraud networks associated with your applicants.
- In an applicant profile, scroll down to the Applicant Networks block and find information on the fraud networks related to the applicant.
The following table describes network properties available in the Dashboard:
| Property name | Description |
|---|---|
Network ID |
Shows a unique identifier of a network. |
Created |
Contains information on the date when a network was created. |
| Modified | Shows the date when the last applicant was added to the network. |
| Pattern |
Indicates the reasons for network creation and its similarities:
|
| Stats |
Shows the statistics based on the following parameters:
|
| Notes | Contains the notes that you have added to the case including the attached tags. |
Results can be downloaded as a CSV report as well and will contain information on all applicants included in the network. The following data will be available in the report:
| Value in report | Description |
|---|---|
id | A unique network identification number. |
createdAt | The time and date of the network creation. |
review.reviewStatus | A current verification status. |
review.reviewResult.reviewAnswer | A final verification result displaying the GREEN or RED status:
|
externalUserId | A unique applicant identifier in your system. |
addedAt | The time and date when the applicant was added to the network. |
View network data as table, chart, or map
When checking the network data, you can switch between the table and chart views:
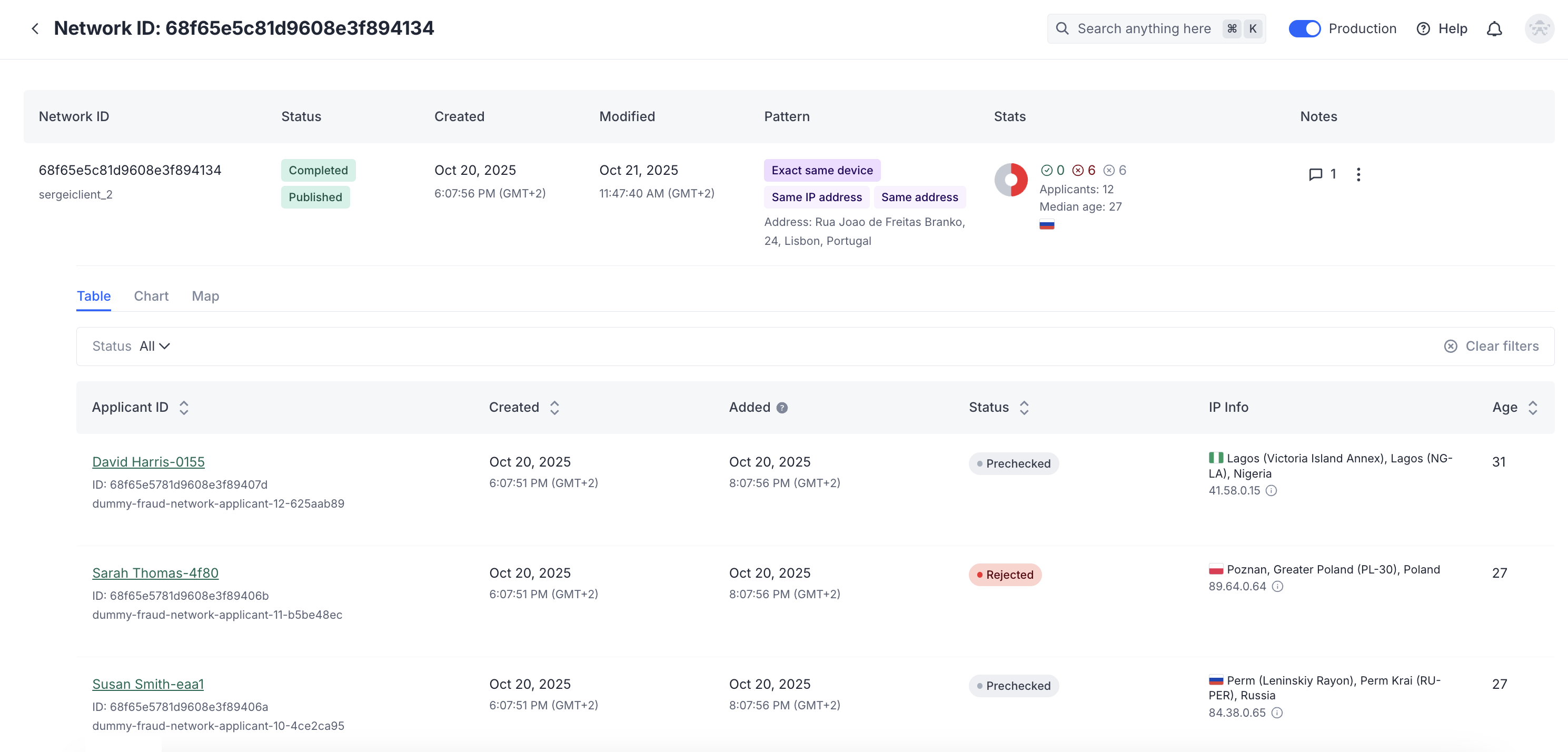
The table view shows the list of applicants with the links and all related information.
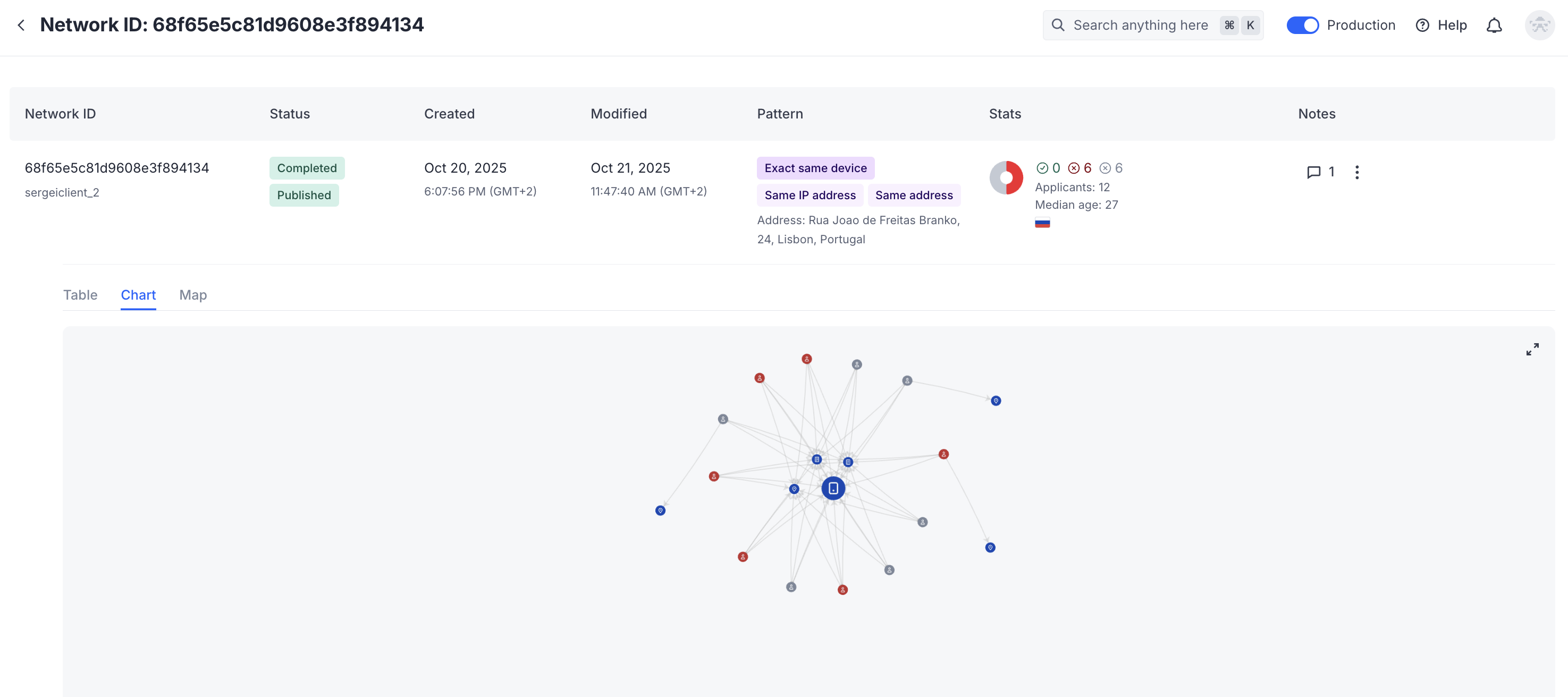
The chart displays applicants, their IP addresses, device fingerprints, and various templates as nodes connected by edges.
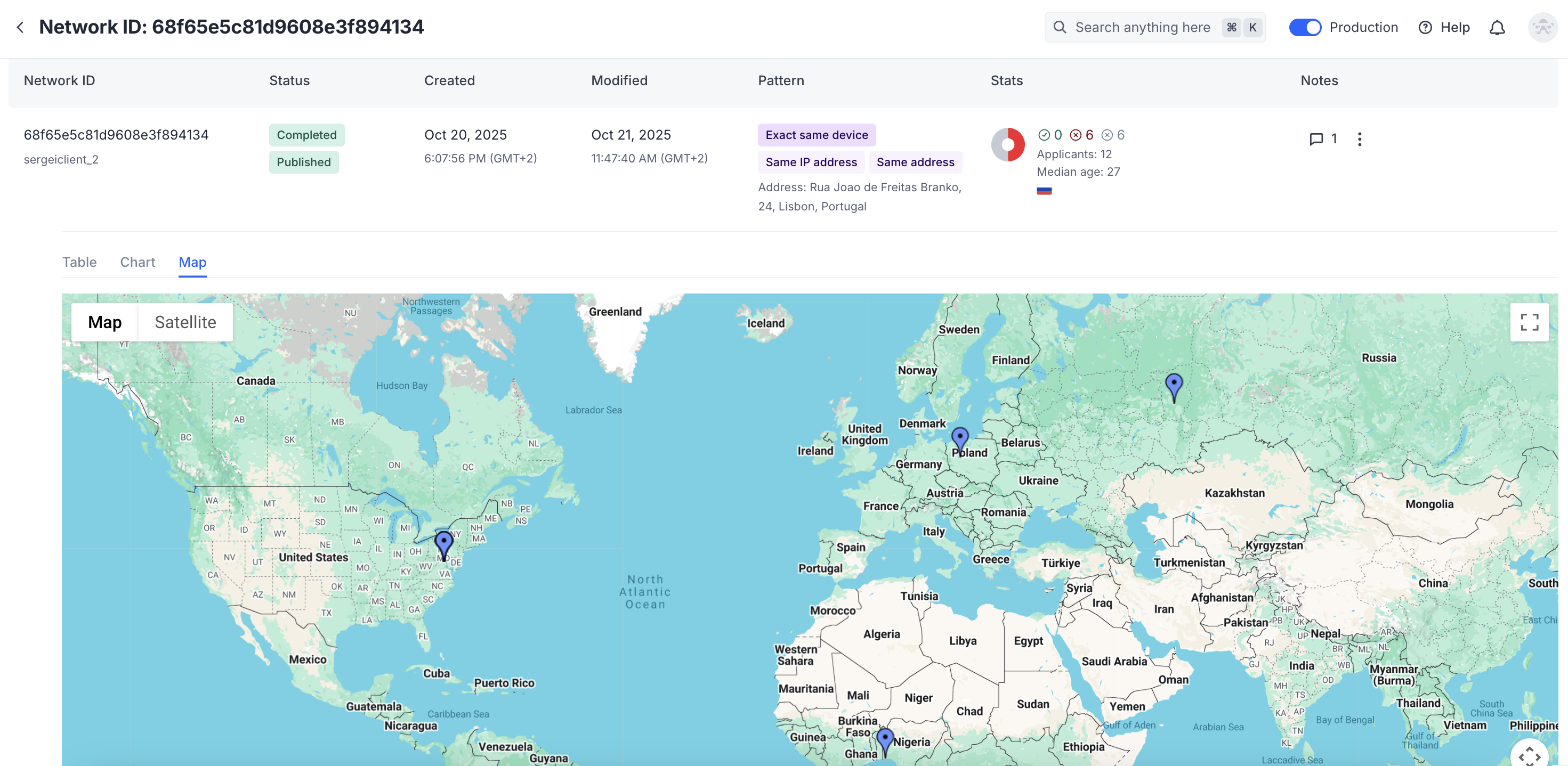
The map view shows the applicants’ locations on a global map based on their detected IP addresses.
Updated 5 days ago