Integrate with Okta
Streamline user authentication with a multifunctional service.
Okta is a cloud-based identity and access platform that allows organizations to securely manage user access to various applications and services. It enables the simplification of user authentication and authorization processes, as well as enhances security by ensuring that users have the right level of access to systems and data.
Upon Okta integration, you will be able to:
- Use single sign-on (SSO). Okta enables users to access multiple applications with a single set of login credentials.
- Configure multi-factor authentication (MFA). Okta offers MFA options, such as biometric verification or one-time passcodes, to add an extra layer of security.
- Secure data usage. Okta provides tools for monitoring user activity and detecting suspicious behavior.
- Centralize access management. Okta provides a platform for managing user access to multiple applications, making it easier to control permissions and security policies across the organization.
Get started with Okta integration
To integrate with Okta, you need to start with setting up your Okta account, following the steps below. After setting it up, you will have all the information necessary to complete the integration from our side.
In Okta
In the Okta Dashboard, you need to create and set up your integration:
- Create a new app integration:
- In the OKTA Dashboard, go to Applications and click Create App Integration.
- When a pop-up window appears, select SAML 2.0 and proceed to the next step.
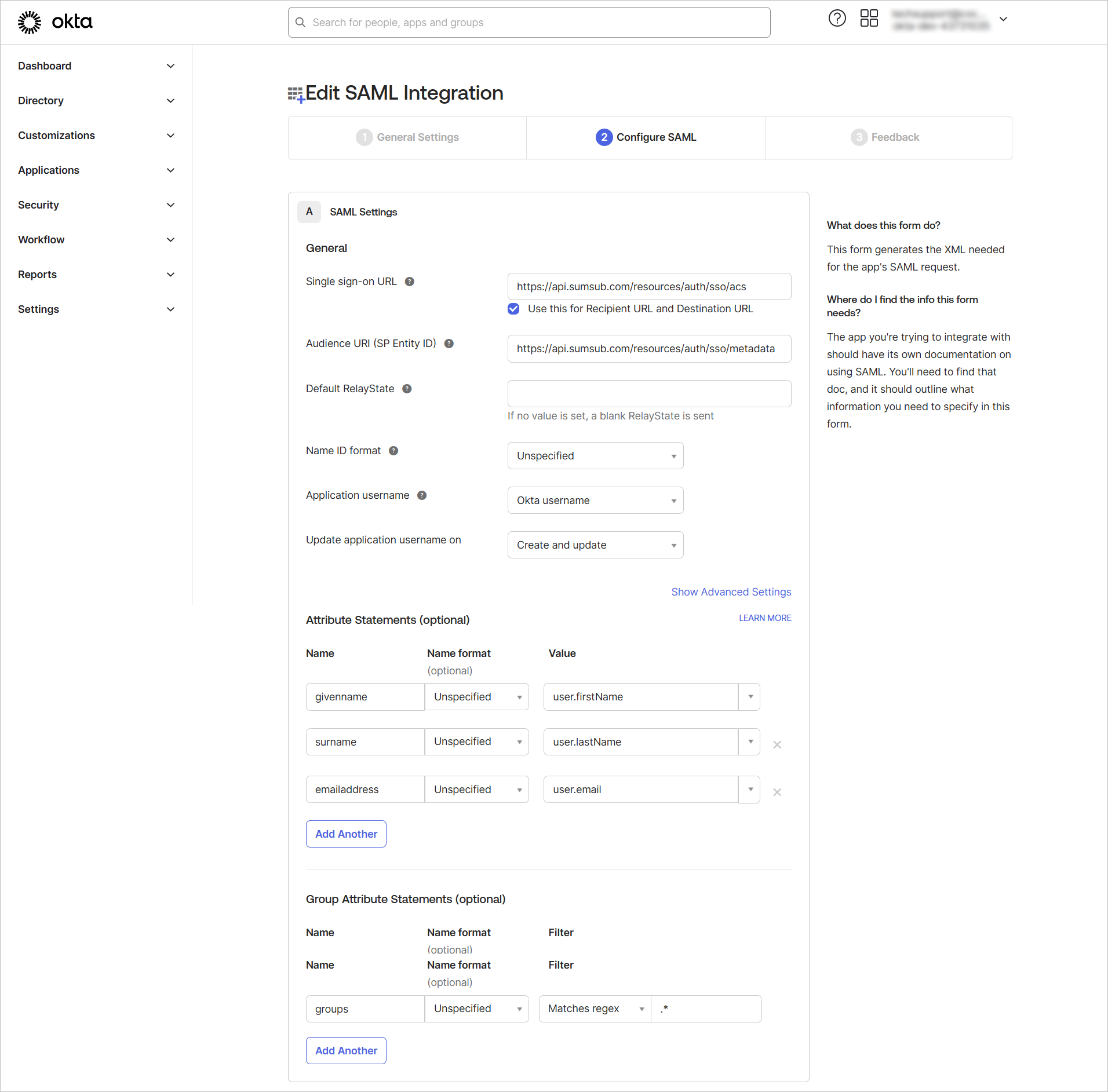
- Edit SAML integration:
- In the General Setting tab, enter the name of the integration.
- Navigate to Configure SAML:
- Within the General section, fill in Single sign-on with https://api.sumsub.com/resources/auth/sso/acs.
- In Audience URI (SP Entity ID), enter the following: https://api.sumsub.com/resources/auth/sso/metadata.
- Fill in Attribute Statements with your given name, last name, and email address. These fields are necessary to complete since our system will use this data to pull up information about a particular user.
- In Group Attribute Statements, specify the name of the group attribute.
- View created integration:
- Go back to Applications and select the integration from the list.
- Navigate to the Sign On tab to view the Metadata details and Certificate fingerprint data.
- Use this data to fill the fields in the Sumsub Dashboard.
In Sumsub
Once your integration is created and configured, transfer the data to the Sumsub Dashboard to complete integration with Okta:
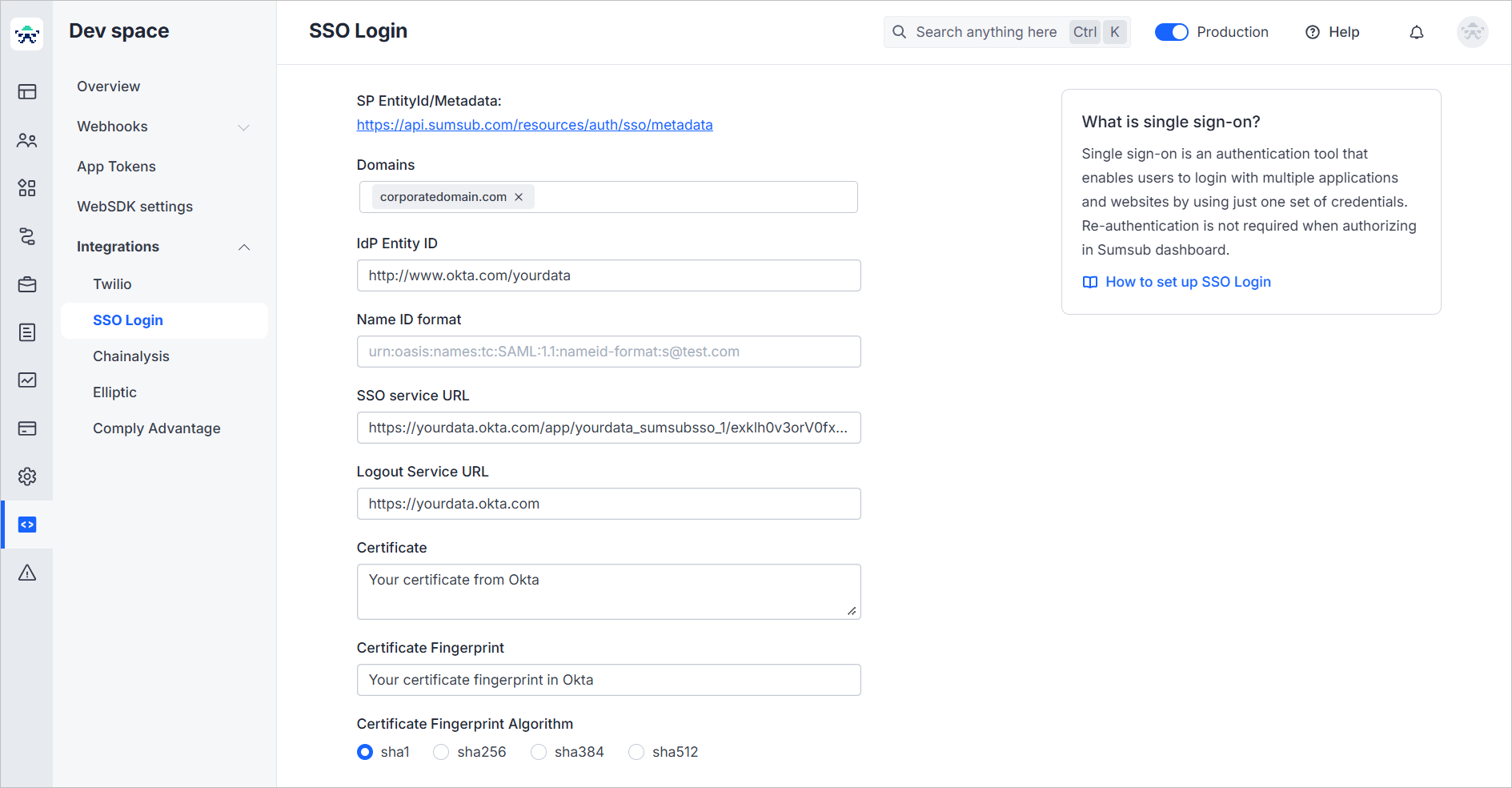
- In the Dashboard, open the SSO Login page.
- Use the corporate email domain in the Domain field.
- For IdP Entity ID, go to the Metadata details in Okta and paste the data from the Issuer field.
- You can leave Name Id Format empty. For more information about this field, see this section.
- For SSO service URL, use data from the Sign on URL field in Okta.
- For Logout service URL, use data from the Sign on URL field in Okta.
- From Metadata details in your Okta account, copy Signing Certificate and paste it in the Certificate field.
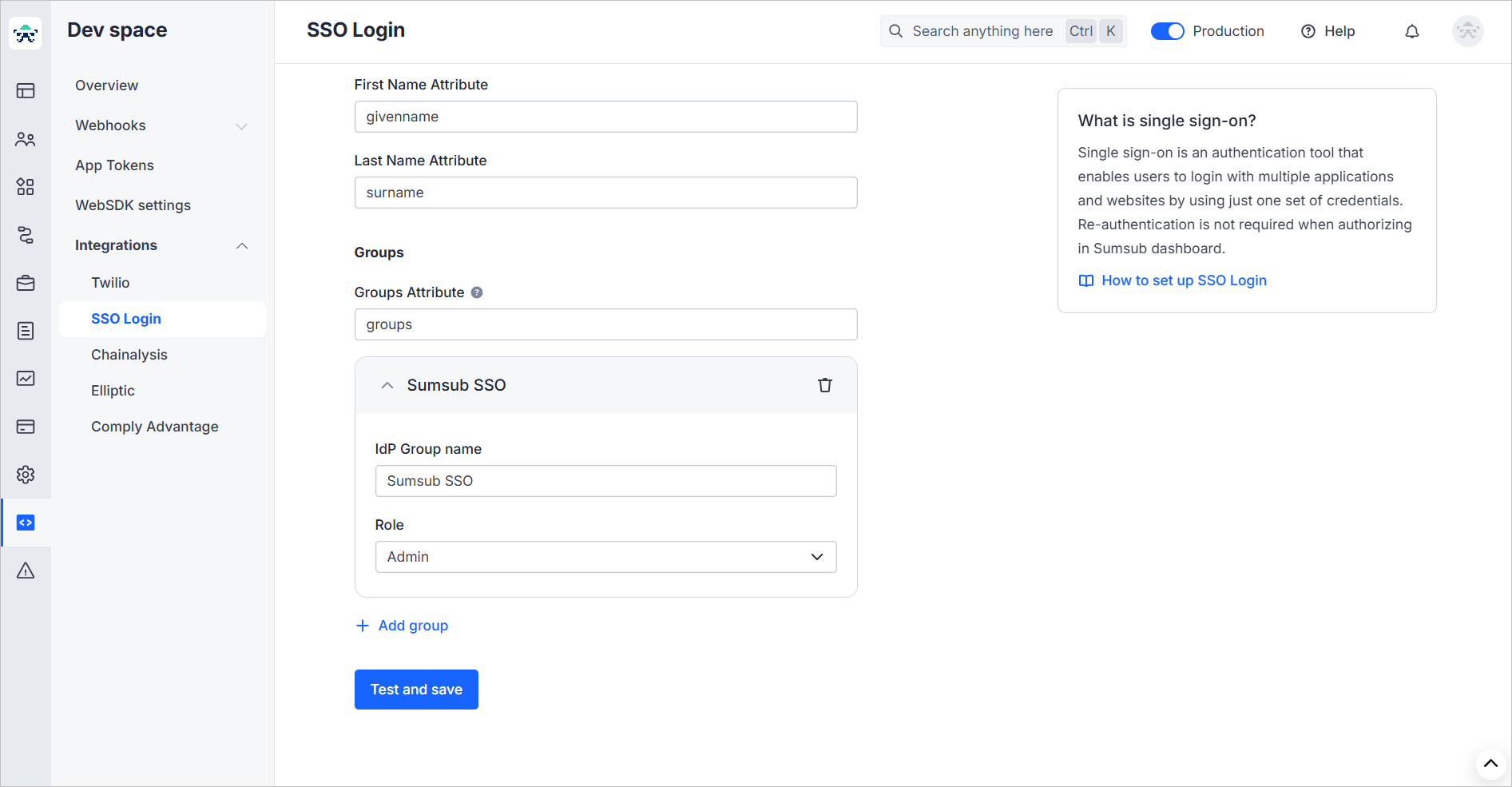
- Fill in Attributes with the data from Attribute Statements in the same format as you specified them in Okta.
- Set up Groups:
- Fill in the Groups Attribute field with the group attribute name from Okta.
- Click Add group to create a group within Sumsub.
- Use IdP Group name to give a name to your group.
- Select a role that will be associated with the group.
- When finished, click Test and save.
Updated 7 months ago